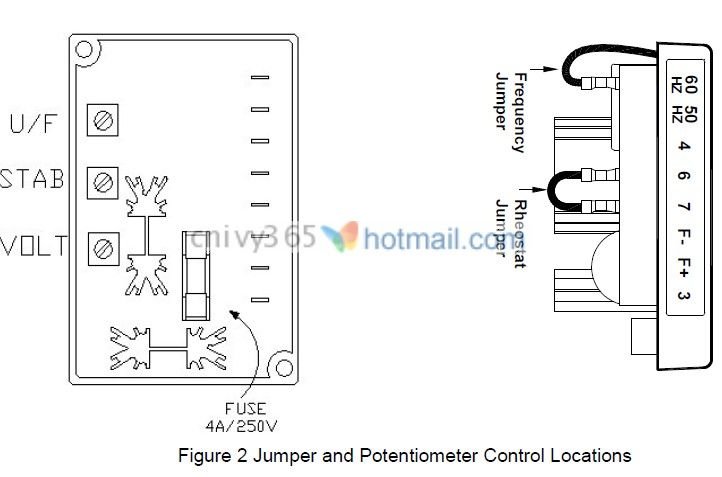
Wiring Diagram For Generator And Voltage Regulator
- Category : Voltage Regulator
- Post Date : January 26, 2026
Wiring Diagram For Generator And Voltage Regulator
Diagram Wiring Diagram For Generator And Voltage Regulator
Download Wiring Diagram For Generator And Voltage Regulator
Malicious email sent to your organization can be cleaned up by the system, through zero hour auto purge (ZAP), or by security teams through remediation actions like move to inbox, move to junk, move to deleted items, soft delete, or hard delete.
Here are some steps to follow to begin regaining control: 1. Regain Email Access. First, unwanted access must be removed and blocked from resulting in any more illicit activities that could cause your data to be compromised, stolen, or deleted. You can do this by: Reset user’s password.
Find and Delete inbox rules from users in Exchange online. Create pliance Search Policy to determined how many emails were sent from the user that matches the subject. Have the option to purge the email from users mailboxes. Project can be found on github here:
Malicious email sent to your organization can be cleaned up by the system, through zero hour auto purge (ZAP), or by security teams through remediation actions like move to inbox, move to junk, move to deleted items, soft delete, or hard delete.
Learn how to report phishing and suspicious emails in supported versions of Outlook using the built in Report button.
Before recovering lost data, the goal is to stop the infection and regain control of our Exchange 365 email account and related apps. Take the following actions to start taking back control:
Microsoft 365, used by over a million organizations globally, has become a prime target for phishing attacks due to its widespread adoption and centrality to business operations. A single successful phishing email can lead to credential theft, ransomware deployment, business email compromise (BEC), or widespread data exfiltration.
Late in 2024, Microsoft showed up in more phishing scams than any other brand—35% of them, to be exact. And despite built in defenses like Exchange Online Protection and Defender for Office 365, a lot of those fake messages still made it through. It’s something attackers count on.
Admins can work with all types of quarantined messages for all users, including messages that were quarantined as malware, high confidence phishing, or as a result of mail flow rules (also known as transport rules).
In this detailed tutorial, you'll learn how to configure Anti Phishing Policies in Exchange Online to safeguard your users from impersonation, spoofing, and targeted phishing emails.
3 way switch,3 way switch wiring,3 way switch wiring diagram pdf,3 way wiring diagram,3way switch wiring diagram,4 prong dryer outlet wiring diagram,4 prong trailer wiring diagram,6 way trailer wiring diagram,7 pin trailer wiring diagram with brakes,7 pin wiring diagram,alternator wiring diagram,amp wiring diagram,automotive lighting,cable harness,chevrolet,diagram,dodge,doorbell wiring diagram,ecobee wiring diagram,electric motor,electrical connector,electrical wiring,electrical wiring diagram,ford,fuse,honeywell thermostat wiring diagram,ignition system,kenwood car stereo wiring diagram,light switch wiring diagram,lighting,motor wiring diagram,nest doorbell wiring diagram,nest hello wiring diagram,nest labs,nest thermostat,nest thermostat wiring diagram,phone connector,pin,pioneer wiring diagram,plug wiring diagram,pump,radio,radio wiring diagram,relay,relay wiring diagram,resistor,rj45 wiring diagram,schematic,semi-trailer truck,sensor,seven pin trailer wiring diagram,speaker wiring diagram,starter wiring diagram,stereo wiring diagram,stereophonic sound,strat wiring diagram,switch,switch wiring diagram,telecaster wiring diagram,thermostat wiring,thermostat wiring diagram,trailer brake controller,trailer plug wiring diagram,trailer wiring diagram,user guide,wire,wire diagram,wiring diagram,wiring diagram 3 way switch,wiring harness
